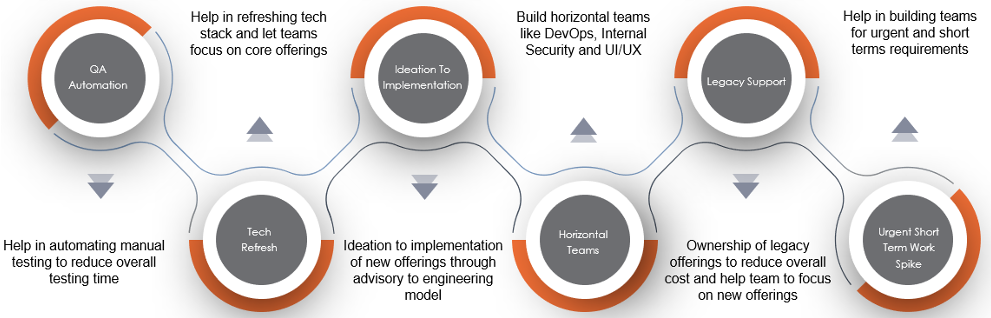
What We Offer
Security breaches cost organizations millions of dollars every single year. It is no longer a choice, but a necessity, to protect your business’ reputation and prevent serious legal issues. At GlobalLogic, we follow a security-first approach to help our customers secure their products and services across all layers from Day 1.