- Services
Technology Capabilities
Technology Capabilities- Product Strategy & Experience DesignDefine software-driven value chains, create purposeful interactions, and develop new segments and offerings
- Digital Business TransformationAdvance your digital transformation journey.
- Intelligence EngineeringLeverage data and AI to transform products, operations, and outcomes.
- Software Product EngineeringCreate high-value products faster with AI-powered and human-driven engineering.
- Technology ModernizationTackle technology modernization with approaches that reduce risk and maximize impact.
- Embedded Engineering & IT/OT TransformationDevelop embedded software and hardware. Build IoT and IT/OT solutions.
- Industries
- GlobalLogic VelocityAI
- Insights
BlogsNovember 6, 2023GlobalLogicOntology – key Enabler of Next-Gen Technologies
Every big or mid-sized company has a proliferation of sites, edge devices, apps, and di...
 BlogsNovember 30, 2023GlobalLogic
BlogsNovember 30, 2023GlobalLogicSmartphone on Wheels
Over the past decade, cars have undergone a significant transformation to provide a mor...

- About
Press ReleaseGlobalLogicSeptember 2, 2024AI adviser speaks the language of the machine
“AI should remain subservient to human needs,” says AI expert Dr Maria Aret...
 Press ReleaseGlobalLogicSeptember 2, 2024
Press ReleaseGlobalLogicSeptember 2, 2024Performance issues holding your mobile app back? You need to ...
Charis Christopoulos, SVP Network and Communication Providers, EMEA at GlobalLogic, exp...

- Careers
Published on October 19, 2021Next-Generation Architecture Best Practices
View all articles Mohammad AshfaqueSenior Lead, EngineeringShareRelated Insights
Mohammad AshfaqueSenior Lead, EngineeringShareRelated Insights GlobalLogic18 December 2025
GlobalLogic18 December 2025 GlobalLogic3 December 2025View All Insights
GlobalLogic3 December 2025View All Insights GlobalLogic1 December 2025Recommended authorsDirector, Industrial BU GSPSenior Vice President & Head of EMEAView all authorsVice President & Consumer Business, Americas GlobalLogic
GlobalLogic1 December 2025Recommended authorsDirector, Industrial BU GSPSenior Vice President & Head of EMEAView all authorsVice President & Consumer Business, Americas GlobalLogicLet's start engineering impact together
GlobalLogic provides unique experience and expertise at the intersection of data, design, and engineering.
Get in touchArchitectureCross-IndustryTechnological advancements are moving at a rapid pace, especially in architecture where practices are constantly evolving. Modern digital transformation requires the latest architectural practices to cater to the growing demands of businesses and for the scaling of software. In this article, we discuss the most important next-gen architectural practices and their benefits:- Token-Based Authentication
- Enhanced DevOps Pipeline
- Containerization based code build model
- Service-Based Architecture
- Limit Stored Procedures
Architecture Best Practices
1. Token-Based Authentication
There are multiple types of authentication techniques, the most common of which is cookie-based. A cookie-based authentication server keeps a record of all database connections on the client side of the cookie, which is stored as a session identifier in the browser.
However, cookie-based authentication has limitations:
- Cookie-based authentication is stateful and impacts scalability.
- Cookies work on a single domain only.
- Tight coupling between client and server.
We recommend the Token-based authentication technique for the next-gen architecture because it is stateless. There are multiple token-based authentication techniques, including the best known and most used JWT (Json web token). The server does not keep a record of users who are logged in or of which JWTs have been issued. Instead, every request on the server is accompanied by a token which the server uses to verify the authenticity of the request.
The token is generally sent as an additional Authorization header in the form of Bearer {JWT}. It can also be sent in either the body or as a query parameter of a POST request. The benefits of using token-based authentication include:
- Stateless authentication mechanism.
- Improved scalability and performance.
2. Enhanced DevOps Pipeline
Next, we have an automated CI/CD (Continuous Integration/Continuous Deployment) pipeline for the codebase. This pipeline should deploy the code to different environments; for example, Dev, QA, Product, etc.
Below is a sample of a CI/CD pipeline for .NET projects. As seen in the pipeline, the code repositories are an AzureDevOps code, which is built through the .NET Nuget package manager tool and tested using NUnit.
The Static code analysis of the code is completed initially using a SonarQube or Resharper tool. It then uses dynamic and security testing performed by the Veracode. This is then deployed using the Octopus tool, which can be further tested via a Functional or a Performance test.
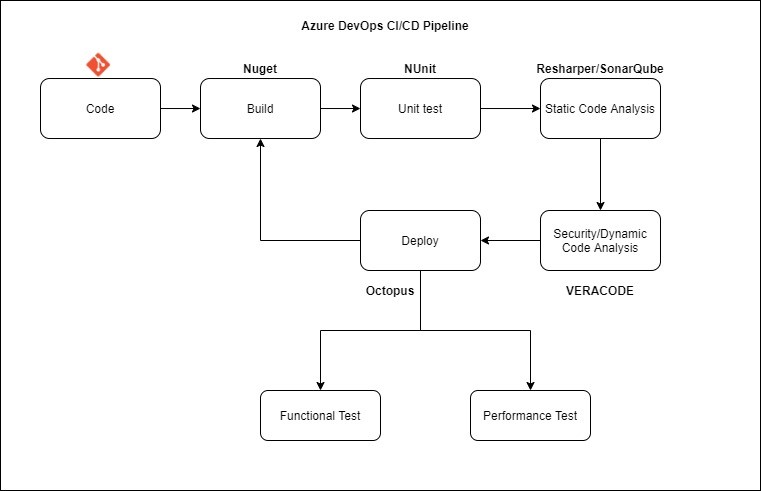
Here are the benefits of using an automated CI/CD pipeline:
- Auto code deployment to various environments, e.g. QA, Pre-Prod, Product.
- Frequent releases.
- Integrated Unit testing in CI/CD Pipeline.
- Integrated Static Code analysis.
- Integrated Security scan.
- Improves code quality and consistent code maintenance process.
3. Containerization-based code to This runtime Docker application build model
Code building and deployment should be done using a containerization-based approach. Docker is the leading containerization technology. The basic container wraps the application and its dependencies to create a runtime environment for the application.
This runtime Docker application contains work that is seamlessly applied to any environment Dev, QA, Prod, etc. Below is a reference to an architecture diagram for the running code of Docker containers.
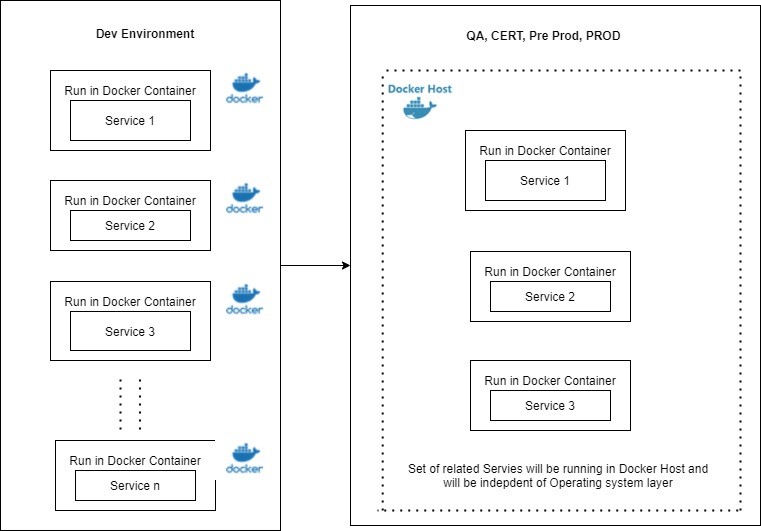
Benefits:
- All Application codes (API/Service) and their dependencies are packaged as a Docker image and run as a Docker container.
- Push Docker images to different environments (QA, CERT, Pre prod, Prod), maintain different Docker versions for images.
- Less time and less operational cost in setting up a new environment.
- This container-based service can be further scaled to be used independently through a container orchestrator service like Kubernetes.
4. Service-Based Architecture
Following a service-based architecture around different business domains enables everything to be serviced as a Rest API or GraphQL, which is easily consumed and reused by other applications. Entire businesses can be approached as a set of independent and accessible APIs.
The following is a reference service-based architecture diagram. The entire business can be seen as a set of Rest API services, which can be easily consumed by business functionalities. This will help to avoid version conflict, remove application compatibility issues, and bring uniformity to the business functionality.
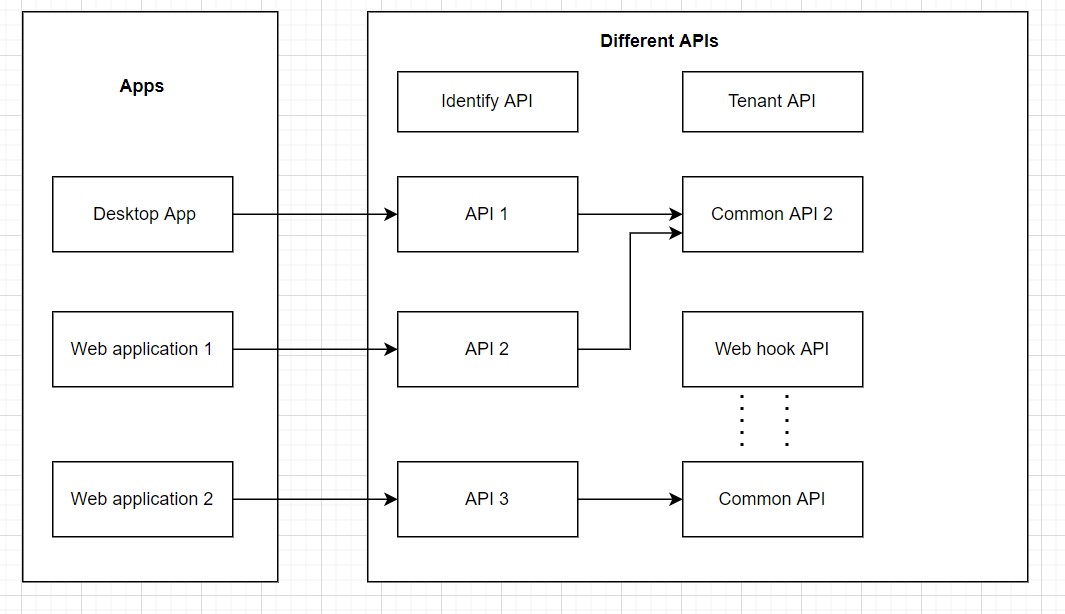
5. Limit Stored Procedures
During the application, stored procedures should be limited as much as possible to avoid:
- SPROCs on a database, which will create a monolithic system that cannot be easily scaled.
- Limitations in automated testing, debugging, error handling, and maintainability.
Apply these steps to reduce stored procedures while moving to the business (API) layer:
- Move the logic of the stored procedure to the business layer of the Rest API/GraphQL handlers. ORM tools like NHibernate/Entity framework can also be used.
- Call relevant SQL scripts through DAPR (Micro ORM) in Rest API.
The benefits of using this approach include easier code maintenance and debugging, error handling, and writing automated unit testing as well as improvements in scalability.
Conclusion
The next-gen architecture practices above can be adapted to any project at any scale, offering several benefits to the project’s maintenance. Adopting these architecture best practices will lead to loosely coupled, stateless applications that are easier to build, maintain, test, and deploy.
 How can I help you?
How can I help you?
Hi there — how can I assist you today?
Explore our services, industries, career opportunities, and more.
Powered by Gemini. GenAI responses may be inaccurate—please verify. By using this chat, you agree to GlobalLogic's Terms of Service and Privacy Policy.
